Azure と某プライベート コンテナ データセンターを VPN で繋いで BGP で経路交換してみたので、忘れないうちにメモっておきます。
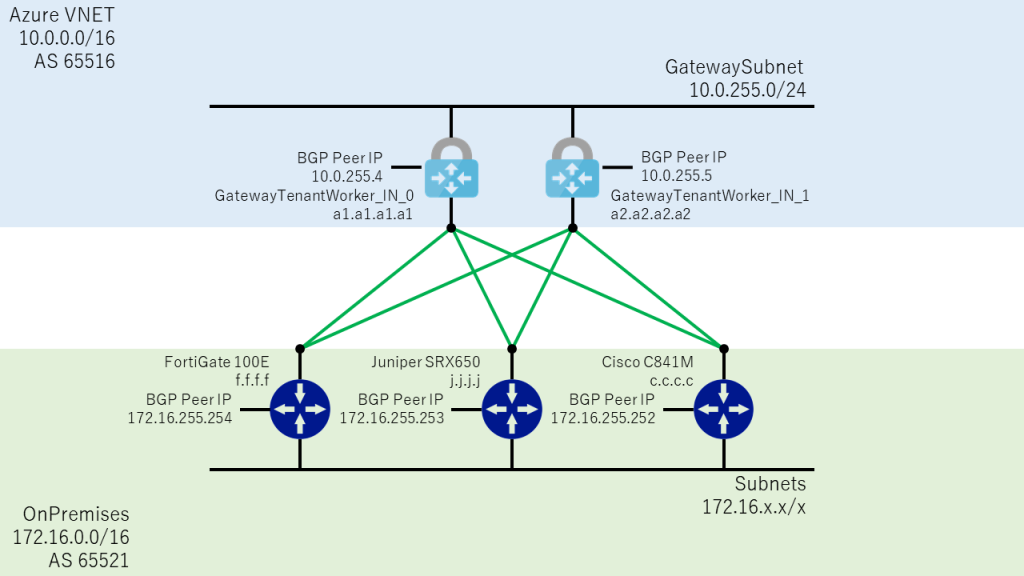
構成図
- Azure 側は VPN Gateway を GwSku1 で Active / Active と BGP を有効化して、Public IPを 2 つ持つ構成。
(下図では a1.a1.a1.a1 / a2.a2.a2.a2) - オンプレミス側は対外接続用のルーター 3 台に固定の Public IP を 1 つずつ用意。
(下図では f.f.f.f / j.j.j.j / c.c.c.c)
Azure 側の構築手順
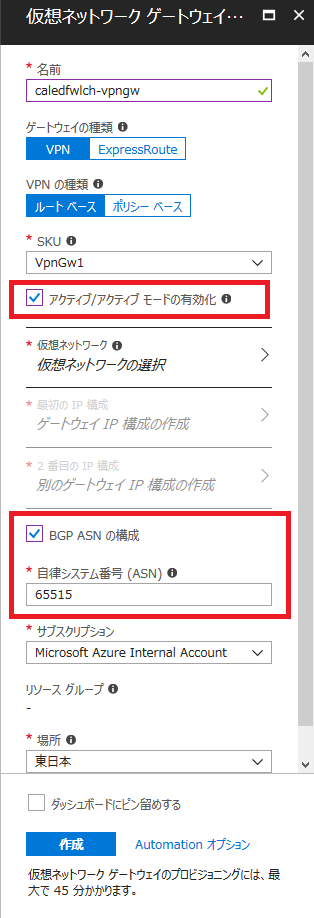
ドキュメントなどを参考に、VPN Gateway を Basic 以外の SKU (Standard / High Performance / VpnGw1 / VpnGw2 / VpnGw3) で作成。
作成時に Active / Active (+ Public IP 2 つ) と、BGP を忘れずに有効化して、Azure 側で使用する AS 番号も設定します。
ちなみに、Azure とオンプレミス間は eBGP で経路交換をすることになるので、オンプレミス側の ASN と同一にはできません。
(その他、Azure で予約されていて使用不可の ASN は FAQ 参照)
- Azure VPN ゲートウェイで、アクティブ/アクティブ S2S VPN 接続を構成する
https://docs.microsoft.com/ja-jp/azure/vpn-gateway/vpn-gateway-activeactive-rm-powershell
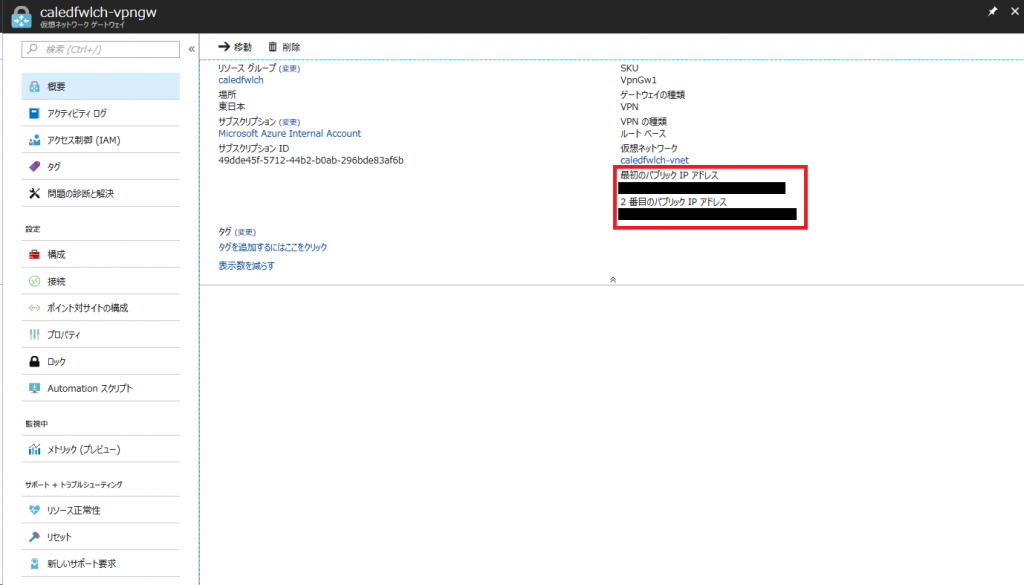
VPN Gateway の作成が完了したら、Public IP が 2 つ付与されていることを確認します。
(同一 VNET 内に VPN Gateway は 2 つ作れないので、Active / Active 構成の VPN Gateway を 1 つ作るだけです)
2 番目の Public IP が隠れていて見えないときは、[もっと見る] をクリックしましょう。
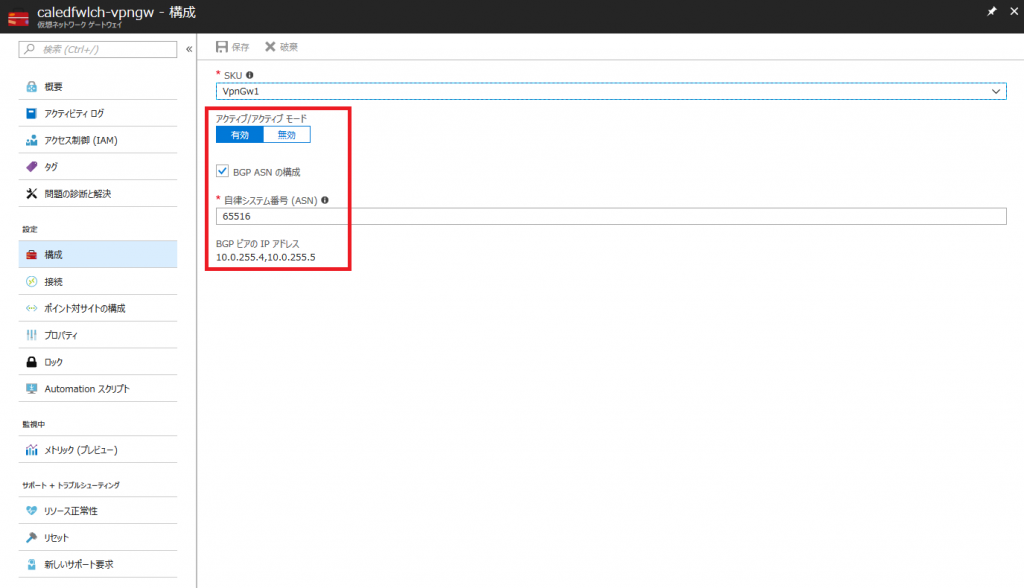
[構成] ブレードで Active / Active と BGP が有効化されていることを確認します。
また、オンプレミス側のルーターを設定する際に使用する BGP Peer IP (オンプレミスから見た Neighbor) をメモっておきます。
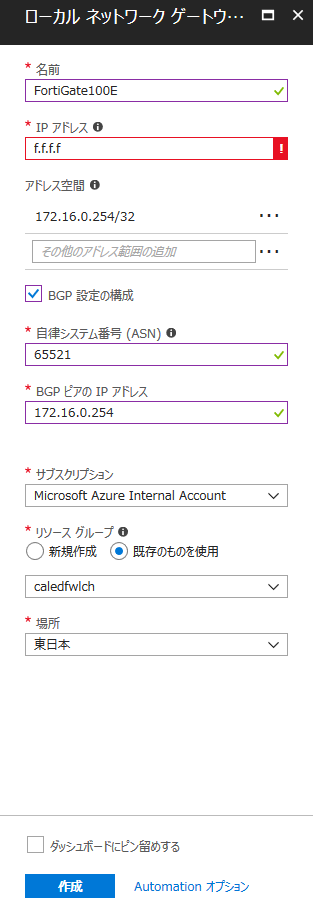
続いて、オンプレミス側の各ルーターの定義を [ローカル ネットワーク ゲートウェイ] として作成します。
各設定項目は以下のような感じで設定しましょう。
- IP アドレス: オンプレミス側のルーターの Public IP
- アドレス空間: オンプレミス側の BGP Peer IP (オンプレミスへの Static Route に使われるため、/32 付きで指定)
- BGP 設定の構成: チェック有
- 自立システム番号 (ASN): オンプレミス側の AS 番号
- BGP ピアの IP アドレス: オンプレミス側の BGP Peer IP (Neighbor の設定には /32 は不要)
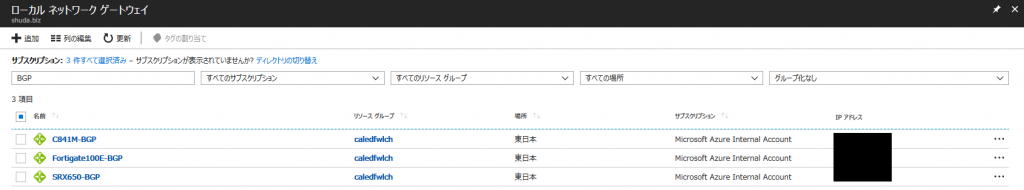
同様に、オンプレミスのルーターの台数分の [ローカル ネットワーク ゲートウェイ] をつくります。(今回は 3 つ)
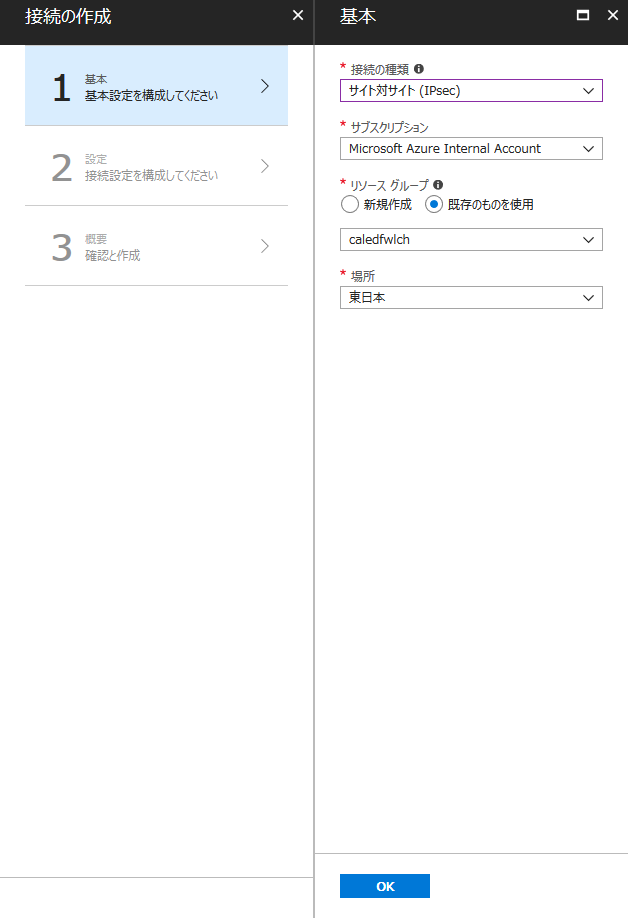
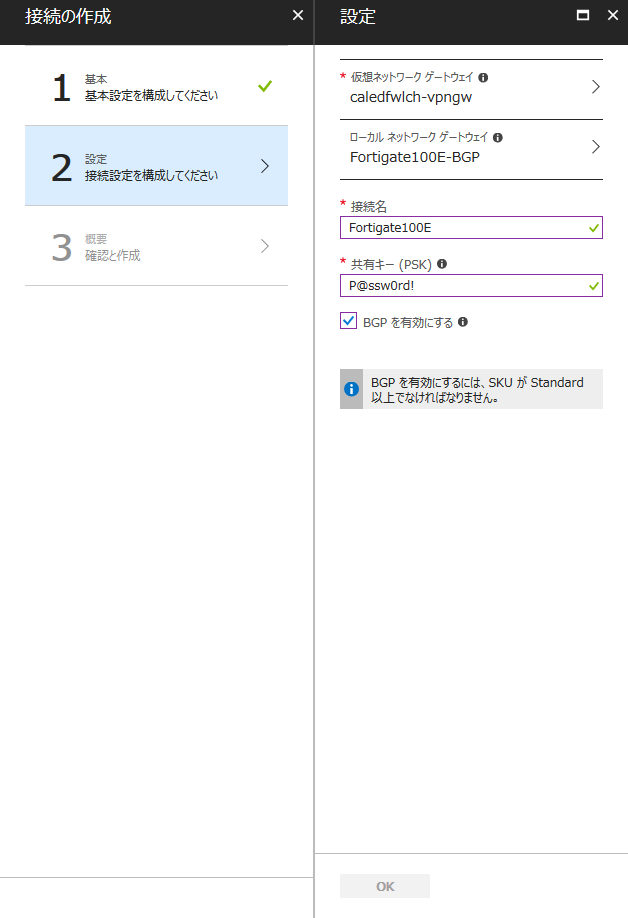
最後に、VPN Gateway とローカル ネットワーク ゲートウェイを [接続] します。
こちらも、BGP のオプションを忘れずに有効化します。
[接続] のリソースも、[ローカル ネットワーク ゲートウェイ] と同じくオンプレミス側の台数分作成します。
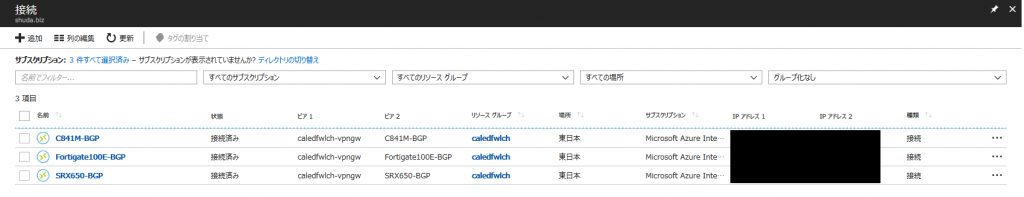
以下の図だと [状態] が [接続済み] になっていますが、オンプレミス側が未設定の場合は [接続中] の表示になっているはずです。
(英語だと Connecting で、接続を試みている最中、すなわち未接続の状態を意味します)
接続状態を読み込んだり更新している最中に、一時的に [状態] が [成功] と表示されますが、これはリソースの定義 (Provisioning State) が正常なことを意味するだけで、VPN がつながっているわけではないので誤解しないように。
オンプレミス側の構成 (FortiGate 100E)
FortiGate との VPN 接続については、CookBook が大変わかりやすいので、こちらを参照。
- IPsec VPN to Microsoft Azure
http://cookbook.fortinet.com/ipsec-vpn-microsoft-azure-56/
今回、Azure 側は Active / Active 構成で 2 つ Public IP があるため、FortiGate 側の VPN の設定も 2 つ定義します。
それから、BGP を使うので、[8. Creating the FortiGate static route] では、VNET のアドレス空間の代わりに、Azure 側の BGP Peer IP (今回は 10.0.255.4 / 10.0.255.5) を設定します。(別に VNET のアドレス空間宛に Static Route を書いてもいいですが、BGP の意味が…)
無事に VPN が接続できていれば、Azure とトンネルが 2 本確立されているはずです。(Phase 1 / 2 あるので、SA は 4 つ)
# diagnose vpn ike status detailed vd: root/0 name: Azure version: 2 connection: 1/712 IKE SA: created 1/713 IPsec SA: created 1/713 vd: root/0 name: AzureBGP version: 2 connection: 1/29 IKE SA: created 4/83 established 4/57 times 0/170/9040 ms IPsec SA: created 4/80 established 4/58 times 0/156/9040 ms vd: root/0 name: AzureBGP2 version: 2 connection: 1/2 IKE SA: created 2/55 established 2/54 times 10/886/26080 ms IPsec SA: created 2/55 established 2/55 times 0/383/21060 ms
VPN のトンネルが張れたら、続いて BGP で経路交換をしてみます。
このあたりは @kongou_ae さんの以下のブログが詳しいので大変参考になりました。
- FortiGateとAzureのVPN GatewayをBGPで接続する
https://aimless.jp/blog/archives/2017-07-17-connect-azure-and-fortgate-with-bgp/
気を付ける点としては、ebgp multihop の設定くらいですかね。(直接 Peer を張っているわけではなく、VPN トンネル越しなので。)
今回は適当に Loopback Interface (172.16.255.254) を作って、オンプレミス側の経路 (172.16.0.0/16) を広報しています。
routing tableに乗っていない経路を広報する関係上、network-import-check を disable していますが、これは構成次第では不要かと。
# show system interface
config system interface
edit "BGPloopback"
set vdom "root"
set ip 172.16.255.254 255.255.255.255
set type loopback
next
# show router bgp
config router bgp
set as 65521
set network-import-check disable
config neighbor
edit "10.0.255.4"
set ebgp-enforce-multihop enable
set next-hop-self enable
set soft-reconfiguration enable
set remote-as 65516
set update-source "BGPloopback"
next
edit "10.0.255.5"
set ebgp-enforce-multihop enable
set next-hop-self enable
set soft-reconfiguration enable
set remote-as 65516
set update-source "BGPloopback"
next
end
config network
edit 1
set prefix 172.16.0.0 255.255.0.0
next
end
BGP の Neighbor が脹れていることを確認します。
# get router info bgp neighbors
BGP neighbor is 10.0.255.4, remote AS 65516, local AS 65521, external link
BGP version 4, remote router ID 10.0.255.4
BGP state = Established, up for 05:11:19
Last read 00:00:33, hold time is 180, keepalive interval is 60 seconds
Configured hold time is 180, keepalive interval is 60 seconds
Neighbor capabilities:
Route refresh: advertised and received (new)
Address family IPv4 Unicast: advertised and received
Address family IPv6 Unicast: advertised and received
Received 479 messages, 0 notifications, 0 in queue
Sent 502 messages, 14 notifications, 0 in queue
Route refresh request: received 0, sent 0
Minimum time between advertisement runs is 30 seconds
Update source is BGPloopback
For address family: IPv4 Unicast
BGP table version 39, neighbor version 38
Index 1, Offset 0, Mask 0x2
Graceful restart: received
Inbound soft reconfiguration allowed
NEXT_HOP is always this router
Community attribute sent to this neighbor (both)
4 accepted prefixes
4 announced prefixes
For address family: IPv6 Unicast
BGP table version 1, neighbor version 1
Index 1, Offset 0, Mask 0x2
Graceful restart: received
Community attribute sent to this neighbor (both)
0 accepted prefixes
0 announced prefixes
Connections established 17; dropped 16
External BGP neighbor may be up to 255 hops away.
Local host: 172.16.255.254, Local port: 13377
Foreign host: 10.0.255.4, Foreign port: 179
Nexthop: 172.16.255.254
Nexthop global: ::
Nexthop local: ::
BGP connection: non shared network
Last Reset: 05:11:24, due to BGP Notification sent
Notification Error Message: (Hold Timer Expired/Unspecified Error Subcode)
BGP neighbor is 10.0.255.5, remote AS 65516, local AS 65521, external link
BGP version 4, remote router ID 10.0.255.5
BGP state = Established, up for 05:14:23
Last read 00:00:25, hold time is 180, keepalive interval is 60 seconds
Configured hold time is 180, keepalive interval is 60 seconds
Neighbor capabilities:
Route refresh: advertised and received (new)
Address family IPv4 Unicast: advertised and received
Address family IPv6 Unicast: advertised and received
Received 494 messages, 0 notifications, 0 in queue
Sent 522 messages, 16 notifications, 0 in queue
Route refresh request: received 0, sent 0
Minimum time between advertisement runs is 30 seconds
Update source is BGPloopback
For address family: IPv4 Unicast
BGP table version 39, neighbor version 38
Index 2, Offset 0, Mask 0x4
Graceful restart: received
Inbound soft reconfiguration allowed
NEXT_HOP is always this router
Community attribute sent to this neighbor (both)
4 accepted prefixes
2 announced prefixes
For address family: IPv6 Unicast
BGP table version 1, neighbor version 1
Index 2, Offset 0, Mask 0x4
Graceful restart: received
Community attribute sent to this neighbor (both)
0 accepted prefixes
0 announced prefixes
Connections established 18; dropped 17
External BGP neighbor may be up to 255 hops away.
Local host: 172.16.255.254, Local port: 24137
Foreign host: 10.0.255.5, Foreign port: 179
Nexthop: 172.16.255.254
Nexthop global: ::
Nexthop local: ::
BGP connection: non shared network
Last Reset: 05:14:27, due to BGP Notification sent
Notification Error Message: (Hold Timer Expired/Unspecified Error Subcode)
BGP で受け取った経路についても確認をしてみます。
Azure 側の BGP Peer IP (10.0.255.4 / 10.0.255.5) から、同じ経路を受け取っていることが分かります。
# get router info bgp neighbors 10.0.255.4 received-routes
BGP table version is 39, local router ID is 172.16.255.254
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.0.0.0/16 10.0.255.4 0 65516 i
*> 172.16.0.0 10.0.255.4 0 0 65516 65521 i
*> 172.16.255.252/32
10.0.255.4 0 65516 i
*> 172.16.255.253/32
10.0.255.4 0 65516 i
*> 172.16.255.254/32
10.0.255.4 0 65516 i
Total number of prefixes 5
# get router info bgp neighbors 10.0.255.5 received-routes
BGP table version is 39, local router ID is 172.16.255.254
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.0.0.0/16 10.0.255.5 0 65516 i
*> 172.16.0.0 10.0.255.5 0 65516 65521 i
*> 172.16.255.252/32
10.0.255.5 0 65516 i
*> 172.16.255.253/32
10.0.255.5 0 65516 i
*> 172.16.255.254/32
10.0.255.5 0 65516 i
Total number of prefixes 5
オンプレミス側の構成 (Juniper SRX650)
SRX との VPN 接続については、ご丁寧に日本語の PDF があったので、こちらの動的ルーティングの設定 (P.30 – )を参照。
- Juniper SRX と Microsoft Azure 仮想ネット ワークとのサイト間 VPN 接続の構成
https://www.juniper.net/jp/jp/local/pdf/implementation-guides/SRX-AzureVPN-v3.pdf
FortiGate と同じく、VPN のトンネルを 2 本 (st0.0 / st0.1) つくり、static route も BGP Peer IP (10.0.255.4 / 10.0.255.5) を設定。
# show security
ike {
proposal azure-phase1-proposal {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
lifetime-seconds 28800;
}
policy azure-policy {
mode main;
proposals azure-phase1-proposal;
pre-shared-key ascii-text "xxxxxxxxxx"; ## SECRET-DATA
}
gateway azure-gw {
ike-policy azure-policy;
address a1.a1.a1.a1;
dead-peer-detection {
interval 10;
threshold 5;
}
local-identity inet j.j.j.j;
external-interface ge-0/0/0;
version v2-only;
}
gateway azure-gw2 {
ike-policy azure-policy;
address a2.a2.a2.a2;
dead-peer-detection {
interval 10;
threshold 5;
}
local-identity inet j.j.j.j;
external-interface ge-0/0/0;
version v2-only;
}
}
ipsec {
proposal azure-phase2-proposal {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy azure-phase2-policy {
proposals azure-phase2-proposal;
}
vpn azure-vpn {
bind-interface st0.0;
vpn-monitor {
optimized;
source-interface st0.0;
destination-ip 10.0.0.0;
}
ike {
gateway azure-gw;
proxy-identity {
local 0.0.0.0/0;
remote 0.0.0.0/0;
service any;
}
ipsec-policy azure-phase2-policy;
}
establish-tunnels immediately;
}
vpn azure-vpn2 {
bind-interface st0.1;
vpn-monitor {
optimized;
source-interface st0.1;
destination-ip 10.0.0.0;
}
ike {
gateway azure-gw2;
proxy-identity {
local 0.0.0.0/0;
remote 0.0.0.0/0;
service any;
}
ipsec-policy azure-phase2-policy;
}
establish-tunnels immediately;
}
}
address-book {
global {
address Azure-VNET 10.0.0.0/16;
address OnPremise-NW 172.16.0.0/16;
}
}
flow {
tcp-mss {
ipsec-vpn {
mss 1350;
}
}
}
policies {
from-zone trust to-zone azure-zone {
policy trust-to-azure-zone {
match {
source-address OnPremise-NW;
destination-address Azure-VNET;
application any;
}
then {
permit;
}
}
}
from-zone azure-zone to-zone trust {
policy azure-zone-to-trust {
match {
source-address Azure-VNET;
destination-address OnPremise-NW;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone azure-zone {
interfaces {
st0.0;
st0.1;
}
}
}
# show interfaces
st0 {
unit 0 {
family inet;
}
unit 1 {
family inet;
}
}
# show routing-options
static {
route 10.0.255.4/32 next-hop st0.0;
route 10.0.255.5/32 next-hop st0.1;
}
無事に VPN が接続できていれば、Azure とトンネルが 2 本確立されているはずです。
# run show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 776365 UP 30964821a7e60fc5 7488a3d455c203f0 IKEv2 a2.a2.a2.a2 776366 UP 1c0743a73adbe841 e903979aed9c53b7 IKEv2 a1.a1.a1.a1 # run show security ipsec security-associations Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <131073 ESP:aes-cbc-256/sha256 9079c193 3565/ unlim U root 500 a1.a1.a1.a1 >131073 ESP:aes-cbc-256/sha256 ac1035a4 3565/ unlim U root 500 a1.a1.a1.a1 <131074 ESP:aes-cbc-256/sha256 83a51222 3507/ unlim U root 500 a2.a2.a2.a2 >131074 ESP:aes-cbc-256/sha256 fa64cbf2 3507/ unlim U root 500 a2.a2.a2.a2
VPN がつながったら、適当に Loopback Interface を作り、ebgp multihop を有効化して、BGP で経路を交換します。
SRX も routing table にない経路を広報しないようなので、static route に 172.16.0.0/16 を入れてみましたが、これでいいのかな…。
あと、今回は FortiGate 側の経路を優先させて、SRX や C841M はバックアップ用にしたいので、AS Path を追加しています。
# show interfaces
lo0 {
unit 0 {
family inet {
address 172.16.255.253/32;
}
}
}
# show routing-options
static {
route 10.0.255.4/32 next-hop st0.0;
route 10.0.255.5/32 next-hop st0.1;
route 172.16.0.0/16 reject;
}
autonomous-system 65521;
# show protocols bgp
local-address 172.16.255.253;
group azure {
type external;
multihop {
ttl 255;
}
neighbor 10.0.255.4 {
export OnPremises;
peer-as 65516;
}
neighbor 10.0.255.5 {
export OnPremises;
peer-as 65516;
}
}
# show policy-options
prefix-list OnPremises {
172.16.0.0/16;
}
policy-statement OnPremises {
term 1 {
from {
protocol static;
route-filter 172.16.0.0/16 exact;
}
then {
as-path-prepend 65521;
accept;
}
}
}
SRX 側から広報している経路と、Azure 側から受け取っている経路を確認します。
AS Path Prepend もきちんと反映されているので問題なさそうです。
> show route advertising-protocol bgp 10.0.255.4 inet.0: 12 destinations, 18 routes (12 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 172.16.0.0/16 Self 65521 [65521] I > show route advertising-protocol bgp 10.0.255.5 inet.0: 12 destinations, 18 routes (12 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 172.16.0.0/16 Self 65521 [65521] I > show route receive-protocol bgp 10.0.255.4 inet.0: 12 destinations, 18 routes (12 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 10.0.0.0/16 10.0.255.4 65516 I * 172.16.255.252/32 10.0.255.4 65516 I 172.16.255.253/32 10.0.255.4 65516 I * 172.16.255.254/32 10.0.255.4 65516 I > show route receive-protocol bgp 10.0.255.5 inet.0: 12 destinations, 18 routes (12 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 10.0.0.0/16 10.0.255.5 65516 I 172.16.255.252/32 10.0.255.5 65516 I 172.16.255.253/32 10.0.255.5 65516 I 172.16.255.254/32 10.0.255.5 65516 I
オンプレミス側の構成 (Cisco C841M)
Cisco IOS との VPN 接続に関しては、GitHub のサンプルやら、Azure ポータルからコンフィグとれるので、そのあたりを参考に。
基本的には FortiGate や SRX と何ら変わらないので、特に難しくないと思います。
crypto ikev2 proposal Azure-proposal encryption aes-cbc-256 aes-cbc-128 3des integrity sha1 group 2 ! crypto ikev2 policy Azure-policy match address local c.c.c.c proposal Azure-proposal ! crypto ikev2 keyring Azure-keyring peer a1.a1.a1.a1 address a1.a1.a1.a1 pre-shared-key xxxxxxxxxx ! peer a2.a2.a2.a2 address a2.a2.a2.a2 pre-shared-key xxxxxxxxxx ! ! ! crypto ikev2 profile Azure-profile match address local c.c.c.c match identity remote address a1.a1.a1.a1 255.255.255.255 match identity remote address a2.a2.a2.a2 255.255.255.255 authentication remote pre-share authentication local pre-share keyring local Azure-keyring lifetime 3600 ! ! crypto ipsec transform-set Azure-TransformSet esp-aes 256 esp-sha-hmac mode tunnel ! crypto ipsec profile Azure-IPsecProfile set transform-set Azure-TransformSet set ikev2-profile Azure-profile ! ! interface Loopback11 ip address 172.16.255.252 255.255.255.255 ! interface Tunnel11 ip address 169.254.0.1 255.255.255.252 ip tcp adjust-mss 1350 tunnel source c.c.c.c tunnel mode ipsec ipv4 tunnel destination a1.a1.a1.a1 tunnel protection ipsec profile Azure-IPsecProfile ! interface Tunnel12 ip address 169.254.0.5 255.255.255.252 ip tcp adjust-mss 1350 tunnel source c.c.c.c tunnel mode ipsec ipv4 tunnel destination a2.a2.a2.a2 tunnel protection ipsec profile Azure-IPsecProfile ! ! router bgp 65521 bgp log-neighbor-changes neighbor 10.0.255.4 remote-as 65516 neighbor 10.0.255.4 ebgp-multihop 255 neighbor 10.0.255.4 update-source Loopback11 neighbor 10.0.255.5 remote-as 65516 neighbor 10.0.255.5 ebgp-multihop 255 neighbor 10.0.255.5 update-source Loopback11 ! address-family ipv4 network 172.16.0.0 neighbor 10.0.255.4 activate neighbor 10.0.255.4 route-map OnPremises out neighbor 10.0.255.5 activate neighbor 10.0.255.5 route-map OnPremises out exit-address-family ! ! ip route 10.0.255.4 255.255.255.255 Tunnel11 ip route 10.0.255.5 255.255.255.255 Tunnel12 ip route 172.16.0.0 255.255.0.0 Null0 200 ! ! ip prefix-list OnPremises seq 5 permit 172.16.0.0/16 ! route-map OnPremises permit 10 match ip address prefix-list OnPremises set as-path prepend 65521 65521 ! ! access-list 101 permit ip 172.16.0.0 0.0.255.255 10.0.0.0 0.0.255.255 access-list 102 permit esp host a1.a1.a1.a1 host c.c.c.c access-list 102 permit udp host a1.a1.a1.a1 eq isakmp host c.c.c.c access-list 102 permit esp host a2.a2.a2.a2 host c.c.c.c access-list 102 permit udp host a2.a2.a2.a2 eq isakmp host c.c.c.c !
VPN の接続状況と、BGP の経路も問題なく交換できました。
#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
2 c.c.c.c/500 a1.a1.a1.a1/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA1, Hash: SHA96, DH Grp:2, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 3600/1478 sec
Tunnel-id Local Remote fvrf/ivrf Status
6 c.c.c.c/500 a2.a2.a2.a2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA1, Hash: SHA96, DH Grp:2, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 3600/1972 sec
IPv6 Crypto IKEv2 SA
#show crypto ipsec sa
interface: Tunnel11
Crypto map tag: Tunnel11-head-0, local addr c.c.c.c
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer a1.a1.a1.a1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 24, #pkts encrypt: 24, #pkts digest: 24
#pkts decaps: 10351, #pkts decrypt: 10351, #pkts verify: 10351
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: c.c.c.c, remote crypto endpt.: a1.a1.a1.a1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/4
current outbound spi: 0xED0535B2(3976541618)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x5CDC6A89(1557949065)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 438, flow_id: Onboard VPN:438, sibling_flags 80000040, crypto map: Tunnel11-head-0
sa timing: remaining key lifetime (k/sec): (4349436/1644)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xED0535B2(3976541618)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 437, flow_id: Onboard VPN:437, sibling_flags 80000040, crypto map: Tunnel11-head-0
sa timing: remaining key lifetime (k/sec): (4349447/1644)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Tunnel12
Crypto map tag: Tunnel12-head-0, local addr c.c.c.c
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer a2.a2.a2.a2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 85613, #pkts encrypt: 85613, #pkts digest: 85613
#pkts decaps: 79209, #pkts decrypt: 79209, #pkts verify: 79209
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: c.c.c.c, remote crypto endpt.: a2.a2.a2.a2
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/4
current outbound spi: 0x6EEC2E88(1860972168)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xBC5C8981(3160181121)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 436, flow_id: Onboard VPN:436, sibling_flags 80000040, crypto map: Tunnel12-head-0
sa timing: remaining key lifetime (k/sec): (4188027/1328)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x6EEC2E88(1860972168)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 435, flow_id: Onboard VPN:435, sibling_flags 80000040, crypto map: Tunnel12-head-0
sa timing: remaining key lifetime (k/sec): (4188019/1328)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
#show bgp
BGP table version is 204, local router ID is 172.16.255.252
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* 10.0.0.0/16 10.0.255.4 0 65516 i
*> 10.0.255.5 0 65516 i
*> 172.16.0.0 0.0.0.0 0 32768 i
r 172.16.255.252/32
10.0.255.4 0 65516 i
r> 10.0.255.5 0 65516 i
* 172.16.255.253/32
10.0.255.5 0 65516 i
*> 10.0.255.4 0 65516 i
* 172.16.255.254/32
10.0.255.4 0 65516 i
*> 10.0.255.5 0 65516 i
#show ip bgp neighbors 10.0.255.4 advertised-routes
BGP table version is 204, local router ID is 172.16.255.252
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 172.16.0.0 0.0.0.0 0 32768 i
Total number of prefixes 1
#show ip bgp neighbors 10.0.255.5 advertised-routes
BGP table version is 204, local router ID is 172.16.255.252
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 172.16.0.0 0.0.0.0 0 32768 i
Total number of prefixes 1
#show ip route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 202.222.13.254 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
B 10.0.0.0/16 [20/0] via 10.0.255.5, 06:35:10
172.16.0.0/16 is variably subnetted, 6 subnets, 3 masks
B 172.16.255.253/32 [20/0] via 10.0.255.4, 05:55:15
B 172.16.255.254/32 [20/0] via 10.0.255.5, 06:35:10
Azure VPN Gateway 側からの確認
最後に、Azure 側からも VPN の接続状況や、BGP の Neighbor が張れて、経路交換ができているか確認します。
> Get-AzureRmVirtualNetworkGatewayConnection -Name FortiGate100E-BGP -ResourceGroupName caledfwlch
Name : Fortigate100E-BGP
ResourceGroupName : caledfwlch
Location : japaneast
Id : /subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/c
onnections/Fortigate100E-BGP
Etag : W/"aece2efa-9d05-4dd8-b928-9634bf6fd463"
ResourceGuid : b85b8f35-8c61-4ad1-ac5f-a908c58b2b0e
ProvisioningState : Succeeded
Tags :
AuthorizationKey :
VirtualNetworkGateway1 : "/subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/
virtualNetworkGateways/caledfwlch-vpngw"
VirtualNetworkGateway2 :
LocalNetworkGateway2 : "/subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/
localNetworkGateways/Fortigate100E-BGP"
Peer :
RoutingWeight : 0
SharedKey : xxxxxxxxxx
ConnectionStatus : Connected
EgressBytesTransferred : 769116
IngressBytesTransferred : 630868
TunnelConnectionStatus : [
{
"Tunnel": "Fortigate100E-BGP_13.78.115.150",
"ConnectionStatus": "Connected",
"IngressBytesTransferred": 296650,
"EgressBytesTransferred": 359947,
"LastConnectionEstablishedUtcTime": "05/03/2018 16:05:48"
},
{
"Tunnel": "Fortigate100E-BGP_52.185.132.141",
"ConnectionStatus": "Connected",
"IngressBytesTransferred": 334218,
"EgressBytesTransferred": 409169,
"LastConnectionEstablishedUtcTime": "05/03/2018 16:02:36"
}
]
> Get-AzureRmVirtualNetworkGatewayConnection -Name SRX650-BGP -ResourceGroupName caledfwlch
Name : SRX650-BGP
ResourceGroupName : caledfwlch
Location : japaneast
Id : /subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/c
onnections/SRX650-BGP
Etag : W/"554cf1f6-bea7-4c38-9905-c7423b332ae4"
ResourceGuid : 1fa22476-2a6e-45f5-89f4-aadb2cfa0c56
ProvisioningState : Succeeded
Tags :
AuthorizationKey :
VirtualNetworkGateway1 : "/subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/
virtualNetworkGateways/caledfwlch-vpngw"
VirtualNetworkGateway2 :
LocalNetworkGateway2 : "/subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/
localNetworkGateways/SRX650-BGP"
Peer :
RoutingWeight : 0
SharedKey : xxxxxxxxxx
ConnectionStatus : Connected
EgressBytesTransferred : 389914
IngressBytesTransferred : 663672
TunnelConnectionStatus : [
{
"Tunnel": "SRX650-BGP_13.78.115.150",
"ConnectionStatus": "Connected",
"IngressBytesTransferred": 308264,
"EgressBytesTransferred": 206306,
"LastConnectionEstablishedUtcTime": "05/03/2018 16:03:48"
},
{
"Tunnel": "SRX650-BGP_52.185.132.141",
"ConnectionStatus": "Connected",
"IngressBytesTransferred": 355408,
"EgressBytesTransferred": 183608,
"LastConnectionEstablishedUtcTime": "05/03/2018 16:04:36"
}
]
> Get-AzureRmVirtualNetworkGatewayConnection -Name C841M-BGP -ResourceGroupName caledfwlch
Name : C841M-BGP
ResourceGroupName : caledfwlch
Location : japaneast
Id : /subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/c
onnections/C841M-BGP
Etag : W/"e1fcee4f-2f5b-4a6b-91be-89d6ee74b5ab"
ResourceGuid : ba300bfb-e09e-4163-98bf-37e37265ce8a
ProvisioningState : Succeeded
Tags :
AuthorizationKey :
VirtualNetworkGateway1 : "/subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/
virtualNetworkGateways/caledfwlch-vpngw"
VirtualNetworkGateway2 :
LocalNetworkGateway2 : "/subscriptions/49dde45f-5712-44b2-b0ab-296bde83af6b/resourceGroups/caledfwlch/providers/Microsoft.Network/
localNetworkGateways/C841M-BGP"
Peer :
RoutingWeight : 0
SharedKey : xxxxxxxxxx
ConnectionStatus : Connected
EgressBytesTransferred : 4209273
IngressBytesTransferred : 4178973
TunnelConnectionStatus : [
{
"Tunnel": "C841M-BGP_13.78.115.150",
"ConnectionStatus": "Connected",
"IngressBytesTransferred": 0,
"EgressBytesTransferred": 325920,
"LastConnectionEstablishedUtcTime": "05/03/2018 16:05:48"
},
{
"Tunnel": "C841M-BGP_52.185.132.141",
"ConnectionStatus": "Connected",
"IngressBytesTransferred": 4178973,
"EgressBytesTransferred": 3883353,
"LastConnectionEstablishedUtcTime": "05/03/2018 16:00:36"
}
]
> Get-AzureRmVirtualNetworkGatewayBGPPeerStatus -VirtualNetworkGatewayName caledfwlch-vpngw -ResourceGroupName caledfwlch | sort Neighbor | ft
Asn ConnectedDuration LocalAddress MessagesReceived MessagesSent Neighbor RoutesReceived State
--- ----------------- ------------ ---------------- ------------ -------- -------------- -----
65516 10.0.255.4 0 0 10.0.255.4 0 Unknown
65516 06:45:41.7296384 10.0.255.4 502 549 10.0.255.5 5 Connected
65521 06:38:08.4475376 10.0.255.4 469 508 172.16.255.252 1 Connected
65521 05:57:19.8491887 10.0.255.4 804 829 172.16.255.253 1 Connected
65521 06:38:08.7202774 10.0.255.4 464 516 172.16.255.254 1 Connected
> Get-AzureRmVirtualNetworkGatewayLearnedRoute -VirtualNetworkGatewayName caledfwlch-vpngw -ResourceGroupName caledfwlch | where Origin -eq EBgp | sort Network, ASPath | ft
AsPath LocalAddress Network NextHop Origin SourcePeer Weight
------ ------------ ------- ------- ------ ---------- ------
65521 10.0.255.4 172.16.0.0/16 172.16.255.254 EBgp 172.16.255.254 32768
65521-65521 10.0.255.4 172.16.0.0/16 172.16.255.253 EBgp 172.16.255.253 32768
65521-65521-65521 10.0.255.4 172.16.0.0/16 172.16.255.252 EBgp 172.16.255.252 32768
> Get-AzureRmVirtualNetworkGatewayAdvertisedRoute -VirtualNetworkGatewayName caledfwlch-vpngw -ResourceGroupName caledfwlch -Peer 172.16.255.254 | sort Network | ft
AsPath LocalAddress Network NextHop Origin SourcePeer Weight
------ ------------ ------- ------- ------ ---------- ------
65516 10.0.255.4 10.0.0.0/16 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.252/32 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.253/32 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.254/32 10.0.255.4 Igp 0
> Get-AzureRmVirtualNetworkGatewayAdvertisedRoute -VirtualNetworkGatewayName caledfwlch-vpngw -ResourceGroupName caledfwlch -Peer 172.16.255.253 | sort Network | ft
AsPath LocalAddress Network NextHop Origin SourcePeer Weight
------ ------------ ------- ------- ------ ---------- ------
65516 10.0.255.4 10.0.0.0/16 10.0.255.4 Igp 0
65516-65521 10.0.255.4 172.16.0.0/16 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.252/32 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.253/32 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.254/32 10.0.255.4 Igp 0
> Get-AzureRmVirtualNetworkGatewayAdvertisedRoute -VirtualNetworkGatewayName caledfwlch-vpngw -ResourceGroupName caledfwlch -Peer 172.16.255.252 | sort Network | ft
AsPath LocalAddress Network NextHop Origin SourcePeer Weight
------ ------------ ------- ------- ------ ---------- ------
65516 10.0.255.4 10.0.0.0/16 10.0.255.4 Igp 0
65516-65521 10.0.255.4 172.16.0.0/16 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.252/32 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.253/32 10.0.255.4 Igp 0
65516 10.0.255.4 172.16.255.254/32 10.0.255.4 Igp 0
細かい部分は非常に怪しい気がしますが、まあ最低限は出来たということで。
間違ってる箇所があれば適宜コメントください。
1 comment for “Azure VPN Gateway (Active / Active) と、FortiGate 100E / Juniper SRX650 / Cisco C841M で VPN を張って、BGP で経路交換してみた”